Defining Propagating State Health Checks
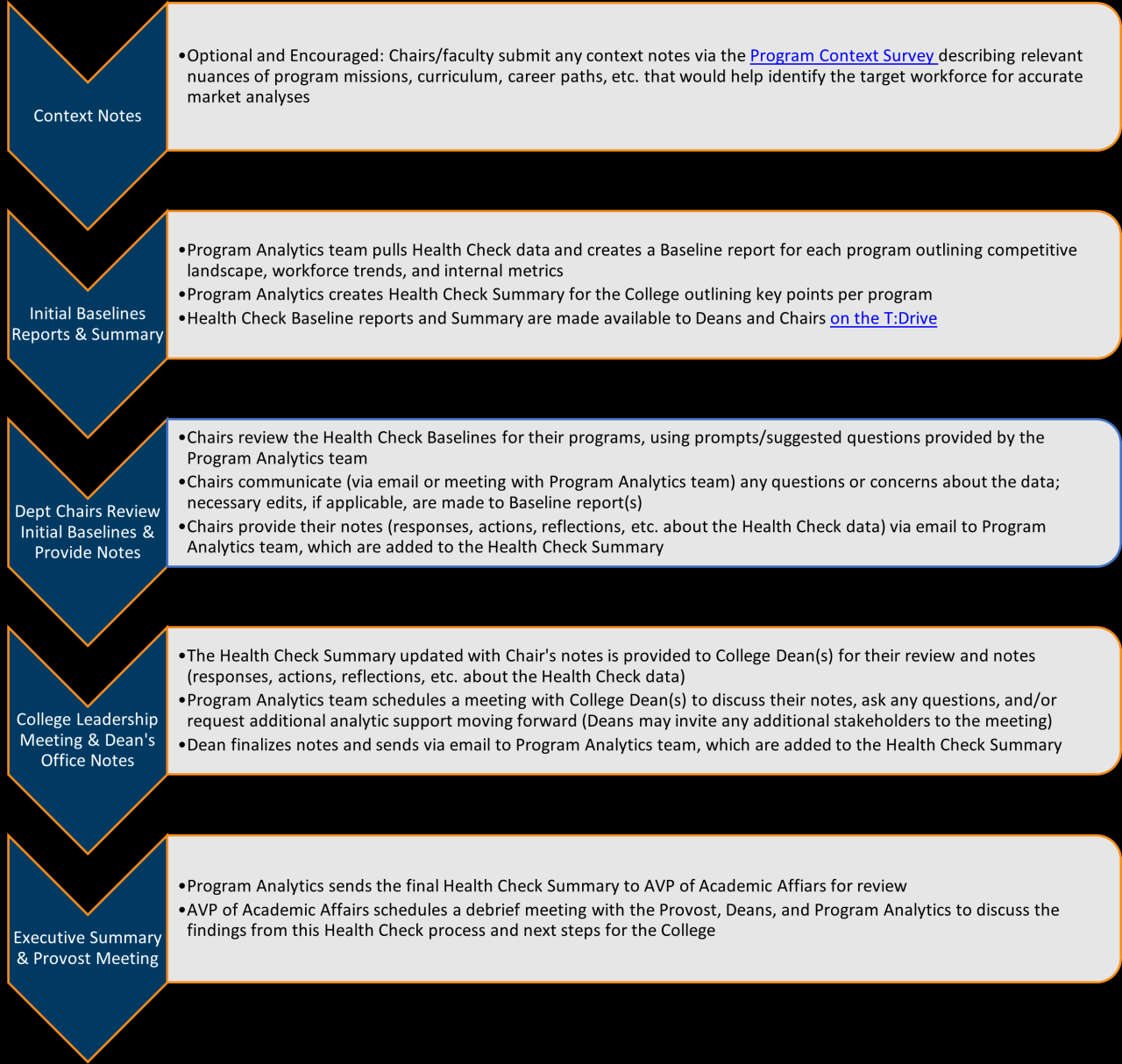
Propagating state health checks are a crucial mechanism in distributed systems, designed to ensure the overall health and availability of the system by monitoring the status of individual components and propagating that status upwards through the system’s hierarchy. These checks go beyond simple binary pass/fail indicators; they actively track and transmit the internal state of each component, providing a richer, more informative picture of the system’s health. This granular level of detail allows for more precise diagnostics and proactive mitigation of potential issues.
Propagating state health checks differ from simpler health checks in their ability to transmit contextual information about the component’s condition. Instead of simply reporting “healthy” or “unhealthy,” these checks provide detailed information about the component’s internal state, such as resource utilization, queue lengths, or error rates. This detailed information allows operators to identify the root cause of problems more efficiently and take targeted corrective actions.
Types of Propagating State Health Checks
The design and implementation of propagating state health checks can vary significantly depending on the specific needs of the system. However, several common patterns emerge. These patterns differ in how they collect and propagate the health information, the level of detail provided, and the mechanism used for propagation.
Characteristics of Different Check Types
One common type involves a hierarchical structure where each component reports its status to its parent. The parent then aggregates the statuses of its children and reports its own aggregated status to its parent, and so on, until the top-level status is reached. This hierarchical approach simplifies the overall monitoring process, providing a clear picture of the health status at each level of the system. Another approach involves a peer-to-peer architecture, where components monitor each other and share their status information through a distributed consensus mechanism. This approach is more resilient to failures, as the loss of a single component doesn’t necessarily impact the overall health monitoring. A third type uses a centralized monitoring system, where all components report their status to a central server. This approach simplifies data collection and analysis but creates a single point of failure.
Essential Scenarios for Propagating State Health Checks
Propagating state health checks are particularly valuable in complex distributed systems where identifying the root cause of failures can be challenging. For example, in a microservices architecture, a failure in one service might cascade through other dependent services, leading to widespread outages. Propagating state health checks provide the detailed information needed to pinpoint the origin of the failure and prevent further cascading effects. Another scenario is in geographically distributed systems, where latency and network connectivity issues can significantly impact performance. Propagating state health checks allow for real-time monitoring of the health and performance of individual components across different geographical locations, providing insights into the impact of network issues on the overall system health. Finally, in systems with high availability requirements, these checks are essential for ensuring that any failures are detected and addressed promptly, minimizing downtime and maintaining service continuity. Consider a large e-commerce platform: a propagating state health check could reveal a slow database connection affecting order processing in a specific region, allowing for rapid intervention before it significantly impacts sales.
Security Considerations: What Is Propogating State Health Checks
Propagating state health checks, while beneficial for monitoring distributed systems, introduce several security risks if not implemented carefully. The distributed nature of these checks, coupled with the transmission of potentially sensitive system information, creates vulnerabilities that require proactive mitigation strategies. This section details these risks and Artikels best practices to ensure the security and integrity of your health check system.
Potential Vulnerabilities and Mitigation Strategies
Unauthorized Access to Health Check Data
Unauthorized access to the propagated health check data could expose sensitive information about the system’s operational status, potentially leading to targeted attacks or service disruptions. This data might reveal resource utilization, application performance metrics, or even configuration details. Mitigation strategies include encrypting the health check data both in transit (using TLS/SSL) and at rest (using encryption at the database level). Implementing robust access control mechanisms, such as role-based access control (RBAC), limits access to authorized personnel only. Regular security audits and penetration testing can identify and address vulnerabilities before exploitation.
Data Integrity and Confidentiality
Ensuring the integrity and confidentiality of the propagated state information is paramount. Malicious actors could tamper with the health check data to mask system failures or create false alarms, leading to inaccurate monitoring and potential outages. To maintain data integrity, digital signatures or message authentication codes (MACs) can be used to verify the authenticity and integrity of the health check messages. Confidentiality can be ensured through encryption, as mentioned previously. Regular verification of the integrity of the health check system itself is crucial, using techniques such as checksum verification.
Denial-of-Service (DoS) Attacks, What is propogating state health checks
A flood of malicious health check requests can overwhelm the system, leading to a denial-of-service (DoS) attack. This could be achieved by sending numerous invalid or malformed requests, exhausting system resources. Mitigation involves implementing rate limiting mechanisms to restrict the number of requests from a single source or IP address within a given time frame. Employing robust input validation techniques can help prevent attacks from exploiting vulnerabilities in the health check processing logic. Furthermore, distributed denial-of-service (DDoS) mitigation techniques, such as using a content delivery network (CDN) with DDoS protection, might be necessary for large-scale deployments.
Best Practices for Securing Propagating State Health Checks
Implementing robust security measures is crucial to protect the integrity and confidentiality of propagated state health checks. The following best practices should be considered:
- Employ strong encryption for data in transit and at rest.
- Implement robust authentication and authorization mechanisms, such as RBAC.
- Utilize digital signatures or MACs to ensure data integrity.
- Implement rate limiting to prevent DoS attacks.
- Regularly perform security audits and penetration testing.
- Use secure communication protocols (e.g., HTTPS).
- Monitor health check traffic for anomalies and suspicious activity.
- Keep the health check system and its dependencies up-to-date with security patches.
- Follow the principle of least privilege, granting only necessary access to the health check data.

Tim Redaksi